SeKVM is the primary formally verified system for cloud computing. Formal verification is a crucial step as it’s the technique of proving that software program is mathematically appropriate, that this system’s code works because it ought to, and there are not any hidden safety bugs to fret about.
“That is the primary time {that a} real-world multiprocessor software program system has been proven to be mathematically appropriate and safe,” mentioned Jason Nieh, professor of laptop science and co-director of the Software program Techniques Laboratory. “Because of this customers’ information are accurately managed by software program operating within the cloud and are secure from safety bugs and hackers.”
The development of appropriate and safe system software program has been one of many grand challenges of computing. Nieh has labored on completely different points of software program programs since becoming a member of Columbia Engineering in 1999. When Ronghui Gu, the Tang Household Assistant Professor of Laptop Science and an professional in formal verification, joined the pc science division in 2018, he and Nieh determined to collaborate on exploring formal verification of software program programs.
Their analysis has garnered main curiosity: each researchers gained an Amazon Analysis Award, a number of grants from the Nationwide Science Basis, in addition to a multi-million greenback Protection Superior Analysis Initiatives Company (DARPA) contract to additional growth of the SeKVM challenge. As well as, Nieh was awarded a Guggenheim Fellowship for this work.
Over the previous dozen years, there was a great deal of consideration paid to formal verification, together with work on verifying multiprocessor working programs. “However all of that analysis has been carried out on small toy-like programs that no one makes use of in actual life,” mentioned Gu. “Verifying a multiprocessor commodity system, a system in broad use like Linux, has been considered roughly unimaginable.”
The exponential development of cloud computing has enabled firms and customers to maneuver their information and computation off-site into digital machines operating on hosts within the cloud. Cloud computing suppliers, like Amazon, deploy hypervisors to assist these digital machines.
A hypervisor is the important thing piece of software program that makes cloud computing potential. The safety of the digital machine’s information hinges on the correctness and trustworthiness of the hypervisor. Regardless of their significance, hypervisors are difficult — they’ll embrace a complete Linux working system. Only a single weak hyperlink within the code — one that’s nearly unimaginable to detect through conventional testing — could make a system susceptible to hackers. Even when a hypervisor is written 99% accurately, a hacker can nonetheless sneak into that specific 1% set-up and take management of the system.
Nieh and Gu’s work is the primary to confirm a commodity system, particularly the widely-used KVM hypervisor, which is used to run digital machines by cloud suppliers equivalent to Amazon. They proved that SeKVM, which is KVM with some small adjustments, is safe and ensures that digital computer systems are remoted from each other.
“We’ve proven that our system can defend and safe personal information and computing uploaded to the cloud with mathematical ensures,” mentioned Xupeng Li, Gu’s PhD scholar and co-lead creator of the paper. “This has by no means been carried out earlier than.”
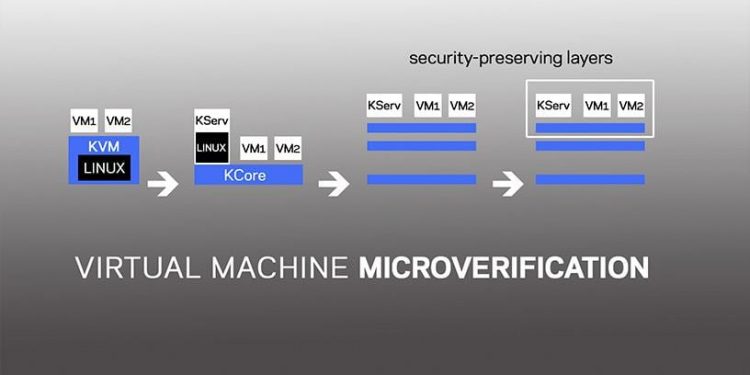
SeKVM was verified utilizing MicroV, a brand new framework for verifying the safety properties of enormous programs. It’s primarily based on the speculation that small adjustments to the system could make it considerably simpler to confirm, a brand new method the researchers name microverification. This novel layering method retrofits an present system and extracts the parts that implement safety right into a small core that’s verified and ensures the safety of your entire system.
The adjustments wanted to retrofit a big system are fairly modest–the researchers demonstrated that if the small core of the bigger system is undamaged, then the system is safe and no personal information will probably be leaked. That is how they have been capable of confirm a big system equivalent to KVM, which was beforehand considered unimaginable.
“Consider a home–a crack within the drywall doesn’t imply that the integrity of the home is in danger,” Nieh defined. “It’s nonetheless structurally sound and the important thing structural system is nice.”
Shih-Wei Li, Nieh’s PhD scholar and co-lead creator of the research, added, “SeKVM will function a safeguard in varied domains, from banking programs and Web of Issues gadgets to autonomous automobiles and cryptocurrencies.”
As the primary verified commodity hypervisor, SeKVM may change how cloud companies must be designed, developed, deployed, and trusted. In a world the place cybersecurity is a rising concern, this resiliency is very in demand. Main cloud firms are already exploring how they’ll leverage SeKVM to satisfy this demand.
Unique Article: Columbia Engineering Group Builds First Hacker-resistant Cloud Software program System
Extra from: Fu Basis College of Engineering and Utilized Science